h1kari, not long ago at ShmooCon 2007,
presented
(*.mp4) his custom Field-programmable gate
array optimized for cracking WEP
and WPA encryption. It performed in some cases over 400% faster than a
Pentium 4 or Athlon64. The reason why the chip performs so remarkably
well is because it has been optimized for such calculations and is a
dedicated to cracking crypto. Dedicated hardware will (in most cases)
always perform faster than a computer CPU, which has to share its
resources among many processes concurrently.
Many people at the conference were very enticed about purchasing such
hardware, which came in a PCMCIA card and could be plugged directly into
a laptop. The crowd let out a sigh of disappointment when h1kari
mentioned the cost... The price? $2000. Why? FPGAs are basically
prototyping equipment. They can be reprogrammed numerous (infinite)
times. It is however, much more expensive than a single, bulk
manufactured integrated circuit. Ryan Clarke suggested and asked h1kari
if he had considered moving to an integrated circuit. The thought
probably never crossed his mind. With an integrated circuit, you don't
have as much flexibility (if at all) to re-programming [read: updating]
its functions, but is generally faster and also consumes less power. If
h1kari can secure an initial investment (most expensive phase) for at
least one thousand chips (which he surely could), he can possibly reduce
the cost to ~$200 each, or even less. I'm sure many people (including
myself) would be willing to pay that amount.
Posted by Marcin on Tuesday, April 17, 2007 in
Security and
Tech.
From F-Secure Weblog : News from the
Lab,
(spoiler: answer below)
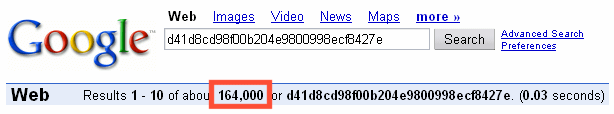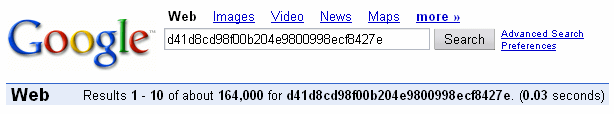
Question of the day: How come you get over 160,000 hits when you
search Google for
"d41d8cd98f00b204e9800998ecf8427e"?
Pretty much the same thing for
"da39a3ee5e6b4b0d3255bfef95601890afd80709".
Answers on a self-addressed envelope to 
The answer:
marcin@thinker:~$ touch temp
marcin@thinker:~$ md5sum temp
d41d8cd98f00b204e9800998ecf8427e temp
marcin@thinker:~$ sha1sum temp
da39a3ee5e6b4b0d3255bfef95601890afd80709 temp
Posted by Marcin on Tuesday, April 17, 2007 in
Security.
And the post of the day goes to Mike
Rothman, and his
comments on Javelin's research
survey that
claims 77% of 2750 consumers said they would not shop at stores that
suffered data breaches.
I think this number is crap. Why? The analogy I'll use is drinking,
which is something I can relate to. If you asked me at 10 AM the
morning after a bender whether I'd be drinking again, the answer
would be no. By 7 PM, my headache had abated and I was ready to
rumble again.
Haha, spot on! He then explains his reasoning:
If you ask someone a question when they have still festering road
rash, the answer will be no - every single time. But time heals,
memories fade, and venomous anger yields to forgiveness and
forgetfulness.
Would you shop at TJMaxx or other stores after knowing they suffered
such a massive security breach? Maybe this is just a reminder -- that
cash is still king!
Posted by Marcin on Monday, April 16, 2007 in
Politics,
Privacy and
Security.
LonerVamp had a post yesterday on preventing Firefox from sending
referrer
messages.
I'll add to that and show how you can prevent websites from resizing the
browser window. In about:config, set the value of
dom.disable_window_move_resize to true. Also, in
Tools>Options>Content>Advanced, make sure the checkbox for "Move or
resize existing windows" is unchecked.
Posted by Marcin on Monday, April 16, 2007 in
Tech.
A funny slide taken from Windows WSYP
Project:
- Security is (or will be) your job. Security is your life. You are
security for your org.
- If you wanna be good, there are things you have gotta know--
- How to say "I don't know"
- How to say "That's not allowed" without giving away the fact that
you really don't know
- How to look innocent -- or mean -- really, it's all situational
- How to say "It's not my fault" even though you screwed up the
configuration really good
- How to deflect blame towards others
- How to speak the language of network communications
Posted by Marcin on Monday, April 16, 2007 in
Security.